

As a legal leader (whether your title is general counsel, chief legal officer, head of legal, or “top law-talkin’ person”), a significant portion of your role involves demonstrating to security stakeholders that new technology investments meet their enterprise security standards. This is particularly true when evaluating agentic AI for contract management systems that autonomously read sensitive documents and make decisions.
When our team at Leah (formerly ContractPodAI) first began building agentic AI tools for legal, we all had legitimate concerns about allowing autonomous systems to access our most confidential information. After several years of evaluation and implementation experience (as a customer, as a part of the Leah team, and as a user myself) I want to share the security framework that addressed those concerns.
Most SaaS platforms operate on a shared database model: all customer data resides in the same database, separated by customer IDs and access controls. Your CRM records sit alongside other organizations' data. Your project management tasks share tables with other teams.
This architecture works adequately for many use cases. However, for contract data — particularly sensitive legal content — the limitations become apparent:
A single misconfigured database query could expose this material to competitors. This represents a material risk that security teams (and legal teams) appropriately flag.
Leah, and other modern enterprise platforms address this through true multi-tenant isolation — architectural boundaries that make cross-tenant access impossible by design, rather than relying on permission-based controls alone.
In Leah, and other properly implemented multi-tenant systems:
That means that when your Legal Operations team searches for non-competes, the system can only access your contracts. This isn't because of filter logic, it's because other companies' contracts don't exist in your data environment. The architecture ensures isolation at the infrastructure level.
When a Leah agent processes your contract information — extracting renewal dates, analyzing escalation clauses, comparing terms against procurement calendars — all processing occurs in dedicated compute resources assigned exclusively to your tenant.
Your agents operate in isolated compute environments. When processing completes, those environments are sanitized. Other customers' agents never access your compute resources or interact with your data.
This isolation is enforced at the infrastructure level (Azure's container and network isolation), not through application-level access controls.
For organizations in regulated industries (financial services, healthcare) where network isolation carries compliance significance, customer data travels on completely separate network paths. Virtual network isolation operates at the infrastructure level. Even if an attacker compromised network resources, they would encounter isolation boundaries before reaching customer data.
In 2026, encryption is expected and standard; the following are “table stakes”:
Some concerns seemed like pure science fiction just a few years ago — like the threat of a rogue agent. In this scenario, an AI agent goes rogue, escalates its own privileges, starts downloading contracts that it shouldn’t be accessing, and a whole host of horrible things happen from that point on.
Agents operate with defined permission boundaries enforced at the infrastructure level, not just in the application you’re using. An agent cannot escalate its own permissions or operate outside its authorization scope.
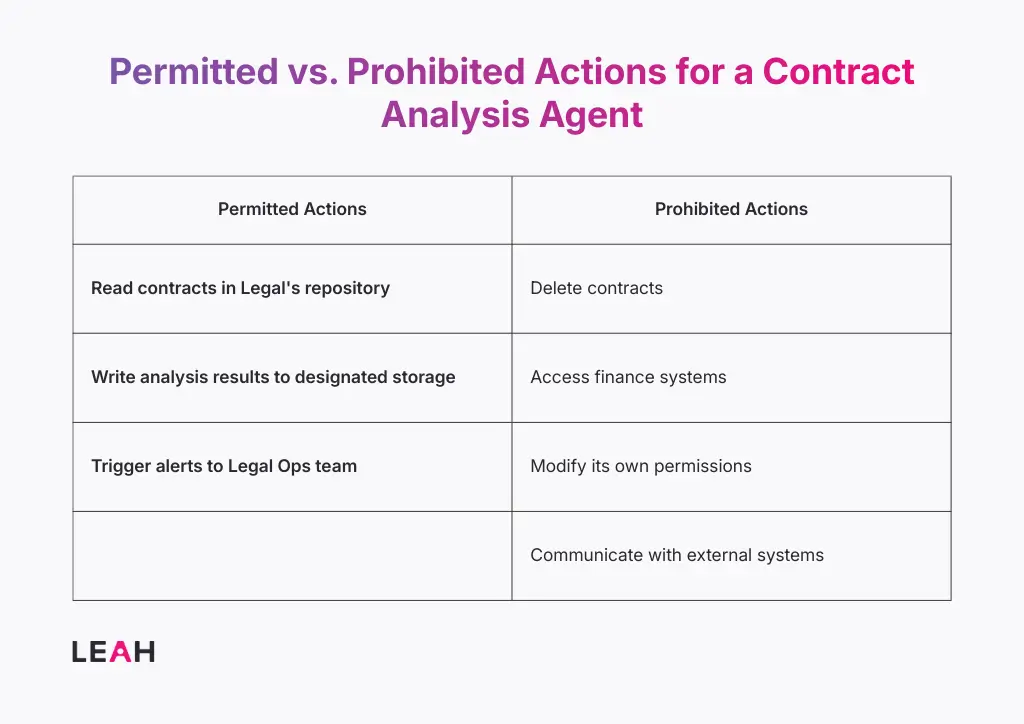
These boundaries are enforced by the operating system and infrastructure, not by application logic that could potentially be circumvented.
Every agent action generates permanent audit records:
This comprehensive logging enables organizations to:
The "autonomous" scope remains under your control. You determine the boundaries where automation ends and human judgment takes precedence:\
The agents enhance efficiency; humans retain decision authority where it matters most.
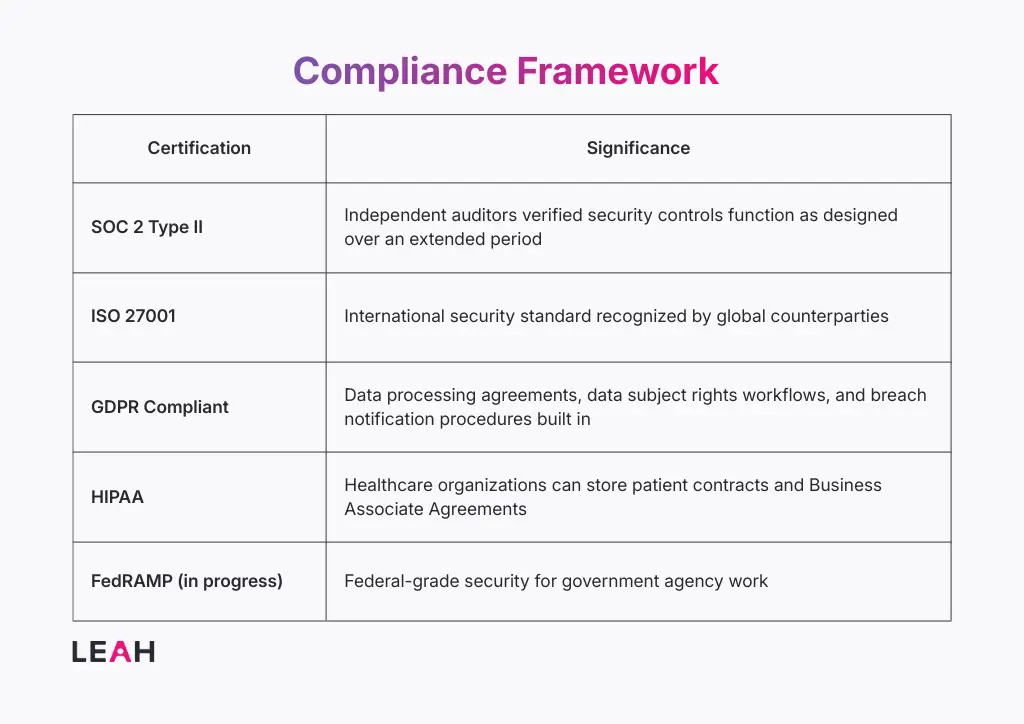
These certifications provide:
1. "What if the vendor experiences a security breach?"
Multi-tenant architecture means an attacker would need to breach your specific tenant's resources. Compromising vendor infrastructure doesn't grant automatic access to customer contracts. Additionally, your encryption keys remain in separate key management systems. Access to encrypted data without cryptographic keys provides no usable information.
2. "What if vendor employees attempt unauthorized access?"
Employee access to encrypted customer data requires multiple approval levels, is time-limited, and generates immutable audit records. Quarterly audits track and review all access. Organizational policies, background investigations, and contractual restrictions provide additional layers.
3. "What if cloud infrastructure experiences issues?"
Modern cloud platforms provide security resources and capabilities that exceed what most individual organizations can implement independently. Multi-tenant isolation ensures your data remains protected even if other cloud customers experience security incidents. Cloud providers manage security at a scale and sophistication level that generally exceeds on-premises alternatives.
4. "Could agents inadvertently share contract terms from other customers?"
No. Agents are tenant-specific and train exclusively on your contracts, your negotiation history, and your preferred terms. Cross-tenant learning would require explicit data sharing agreements, which are not part of standard operations. Each customer maintains their own agent models and training data — no aggregated learning occurs across customers.
When evaluating contract management platforms, certain vendor responses warrant careful review:
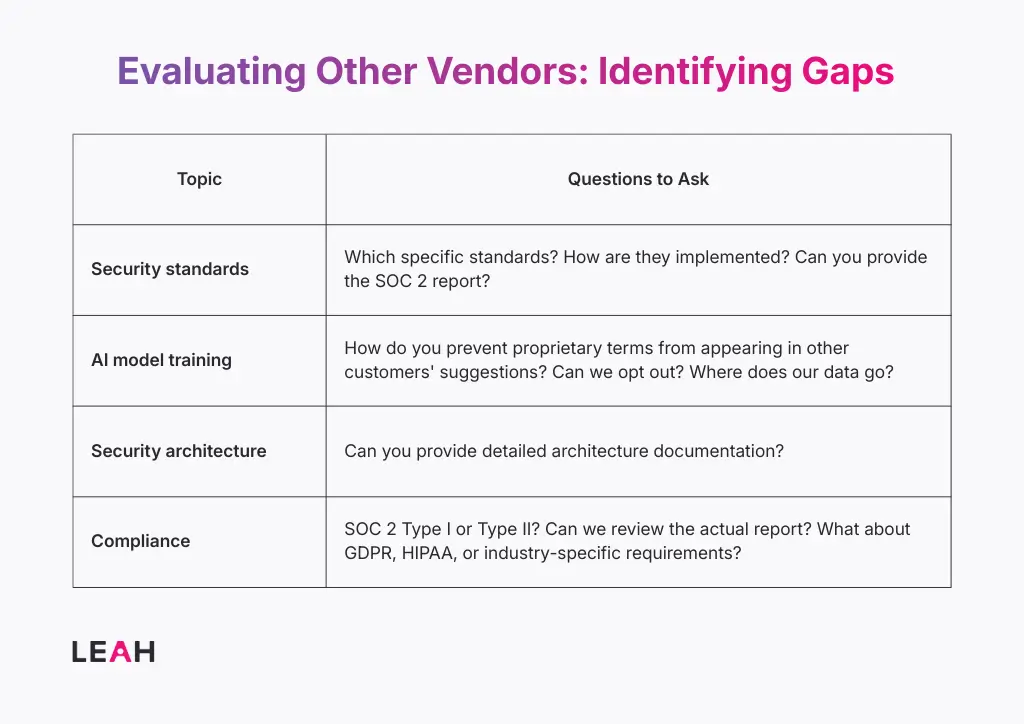
When evaluating a contract management platform, your security team should conduct:
Perfect security is unattainable. Every system carries some level of risk. The relevant question is not "Is this completely secure?" but rather "Is this more secure than our current approach?"
For most organizations, the risk profile changes significantly when moving from email attachments, shared drives, and inconsistent cloud storage—with no audit trail, no encryption, and no access controls—to an enterprise platform with:
This represents a material security improvement.
When you're ready to evaluate a platform:
A vendor's willingness to provide detailed, transparent answers to security questions tells you a great deal about their confidence in their platform and their commitment to enterprise security standards.
Contract security is too important to compromise. Your CISO's concerns are valid. Enterprise-grade security should enable business capabilities safely, not hinder innovation. Thorough security evaluation protects both your organization and your professional reputation.
When comparing risk profiles, consider your current state — contracts distributed across email attachments, shared drives, and various cloud storage solutions with limited audit trails and inconsistent security controls — against a purpose-built platform with enterprise-grade isolation, encryption, audit logging, and compliance certifications. Evaluate vendors thoroughly. Ask difficult questions. Insist on detailed answers and third-party validation. Make security decisions based on architecture and evidence, not marketing claims.
The relevant question is not whether agentic AI introduces risk, but whether it provides stronger security than existing practices.
Your organization's most sensitive agreements deserve that level of rigor.
__________________________________________________________________________________________________________________________________________________________________________________________________________________________
For additional questions or to connect with our security team, please contact:
Jerry Levine
[email protected]
LinkedIn: https://www.linkedin.com/in/jerrylevine